Attention, Next.js developers and users! A **critical authentication bypass vulnerability** has been identified, impacting middleware functions within the popular framework. This alarming flaw has been assigned the reference CVE-2025-29227 and comes with a **CVSS 3.1 score of 9.1**, indicating a severe risk to your applications.
Understanding the Vulnerability: A Potential Attack Vector
The essence of this vulnerability lies in its ability to allow an **unauthenticated attacker to bypass Next.js authorization mechanisms** effortlessly. This loophole could put your entire application at risk if not addressed promptly.
Diving into Technical Details
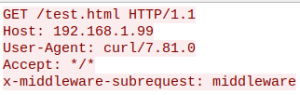
So, what makes this vulnerability tick? The issue resides in an **internal Next.js function** designed to prevent infinite middleware execution loops. When the HTTP header x-middleware-subrequest is present with a specific value (which varies depending on the Next.js version), it effectively allows attackers to sidestep Next.js authorization functionalities.
Versions Affected:
- >= 11.1.4, <= 13.5.6
- >= 14.0, < 14.2.25
- >= 15.0, < 15.2.3
Attack Modelling through MITRE ATT&CK
What is MITRE ATT&CK?
The vulnerability is characterized by its exploitation of public-facing applications, categorized under T1190 (Exploit Public-Facing Application). This highlights the need for heightened security measures for your web applications.
How to Shield Against This Vulnerability with Stormshield Network Security
Protection Against CVE-2025-29227
To safeguard your applications against CVE-2025-29227, Stormshield Network Security (SNS) firewalls offer detection and blocking capabilities with the following IPS signature:
- http:client:header:259: Exploitation of a Next.js middleware vulnerability (CVE-2025-29227)
However, note that **efficient protection requires traffic decryption** to function correctly.
 Confidence index for the protection offered by Stormshield |
Confidence index for the absence of false positives |
Best Practices to Counter the Next.js Vulnerability
Ensuring the security of your application involves timely updates. Here are our **recommended updates** for various Next.js versions:
- For Next.js 15.x, update to version 15.2.3.
- For Next.js 14.x, update to version 14.2.25.
- For Next.js 13.x, update to version 5.9.
- For Next.js 12.x, update to version 12.3.5.
- For any other Next.js versions, we strongly advise **disabling the external usage** of the
x-middleware-subrequestHTTP header via a reverse proxy.
Taking action is essential to protect your applications from this significant vulnerability. **Stay informed, stay secure**, and ensure your Next.js frameworks are up to date to mitigate risks effectively!
For further reading on Next.js vulnerabilities and security measures, check out OWASP or explore the resources available at NIST.






